im a jailbreaker. whatever device. PS3, PSVita, iPhone, iPad, Apple TV, etc. why? because i payed for the device and i want to do what i want with it. also its technically interesting to see behind the scenes. most of these devices run a linux or an OS that is rather similar. there are different CPU architectures (Intel, ARM, PowerPC, etc) which are quite interesting to work with too.
but what does jailbreak mean? in short: a jailbreak removes the software restrictions implemented by the producer of the device. mostly it means you get root privileges and can install additional software, which the manufacturer would not allow.
normal users should not have root or administrative privileges, because the could do harm to a system (without even wanting to). for that reason, jailbreak has a bad reputation and people think it is evil.
but it is not. i use it to customize my iPhone just the way i want it. means, i can install tweaks that make the appearance or the functionality of the iPhone even better. it offers really a lot of options like SSH, a filebrowser, smaller icons on the homescreen, higher resolution, faster animations and a lot of other cool things.
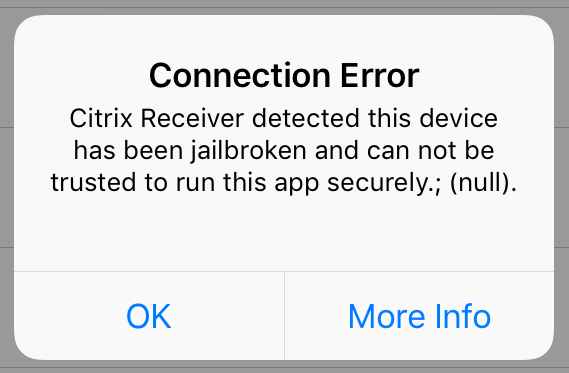
however – if you use an iPhone in a corporate environment, this might not be a desired state and therefore some apps implement a Jailbreak detection.
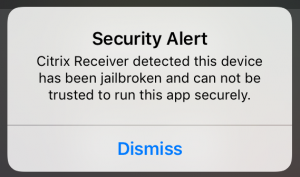
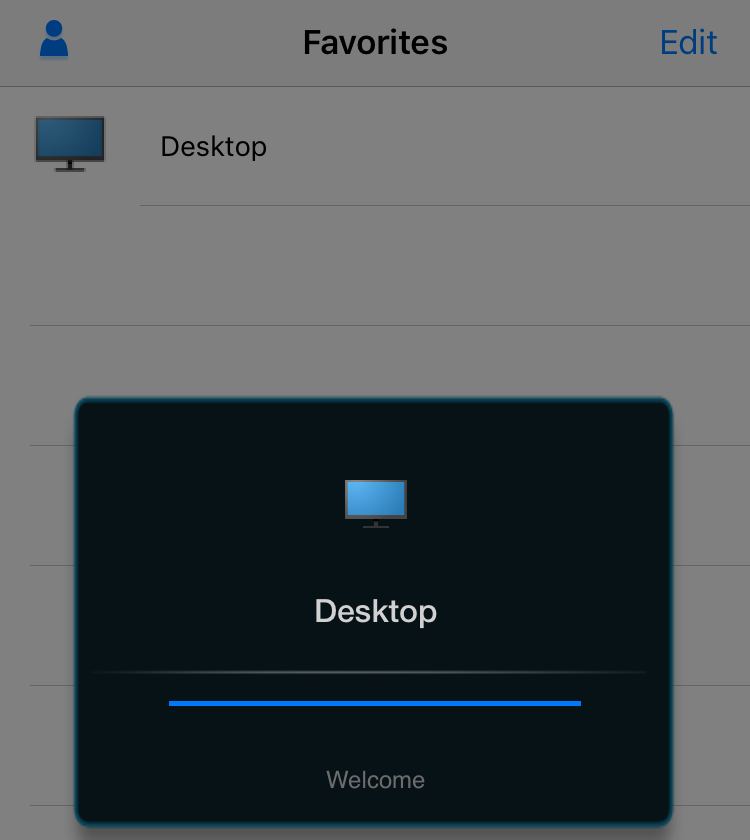
Citrix also did that (i think mainly because of XenMobile) in the iOS Receiver. you can even configure your storefront, to block connections from jailbroken devices completely. here is how to do that: https://docs.citrix.com/en-us/receiver/ios/6/jailbroken-devices.html – but even without this configured, Citrix Receiver will show a Security Alert when launching it on a jailbroken phone:
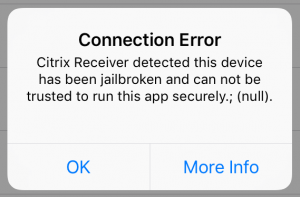
And on trying to connect with the Storefront configuration from Citrix:
that is quite annoying. can we somehow disable that? of course! like i said in the beginning, jailbreaking gives us root access on the device and we can do EVERYTHING. Citrix can only do what Apple allows them and this is not much. Apple iOS is an operating system that has a LOT of security mechanisms like sandboxing, DRM and even worse stuff. a developer can only use a set of functions and is not allowed to access the iOS system with his app. Apple checks every App that is submitted to the store and does reject it when it violates this rule.
on jailbroken iphones there is a framework called cydia substrate which can hook iOS functions and therefore lets you modify the system without binary-patching it.
my plan was, to find out how Citrix detects the jailbreak and then write a tweak to disable or spoof these checks. lets go:
Jailbreak Analysis
to reverse engineer an iOS binary we need following tools:
- Clutch2 (to dump and decrypt the iOS app – removing Apple DRM)
- IDA Pro (to disassemble the decrypted iOS app)
- Theos (to code a tweak)
- A jailbroken Device (atm you can jailbreak up to 10.2.1, depending on your device)
- A Mac with XCode
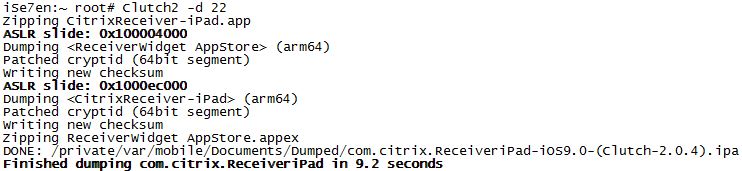
first we have to get a decrypted .ipa of the Citrix Receiver App. we can achieve that using Clutch2 over SSH. when using Yalu jailbreak, it will install SSH already, but its only listening to 127.0.0.1 (for security reasons). to connect over SSH you can use iFunBox with an USB tunnel.
you can copy Clutch2 to /bin/ with iFunBox or SCP and then you need to chmod +x /bin/Clutch2 it – to make it executable. now you can connect with SSH to 127.0.0.1 using the root:alpine credentials (default password).
by running “Clutch2 -i” you get a list of all installed apps. in my case Citrix Receiver was app number 22:
22: Citrix Receiver <com.citrix.ReceiveriPad>
to dump the app, you just need to run “Clutch2 -d 22” (of course the number is not the same on your phone).
you can grab the decrypted ipa from /private/mobile/Documents/Dumped/ with iFunBox or SCP. to unpack the ipa file, you can use 7-zip (any unpacker will work – ipa files are just renamed zip files).
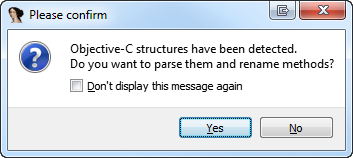
in the Payload\CitrixReceiver-iPad.app folder you can find a “CitrixReceiver-iPad” binary, which is basicly the Receiver itself. we are going to disassemble it in IDA Pro now. launch IDA, select the binary and wait a little. it will show you a popup which asks you:
its very important, that you select yes – this will show us a LOT of informations (function names and objective-c stuff) which makes it much easier to find what we are looking for.
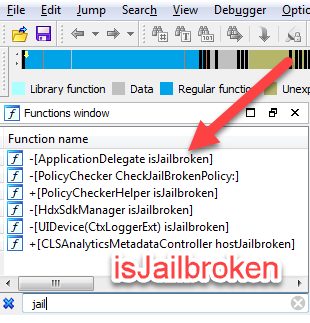
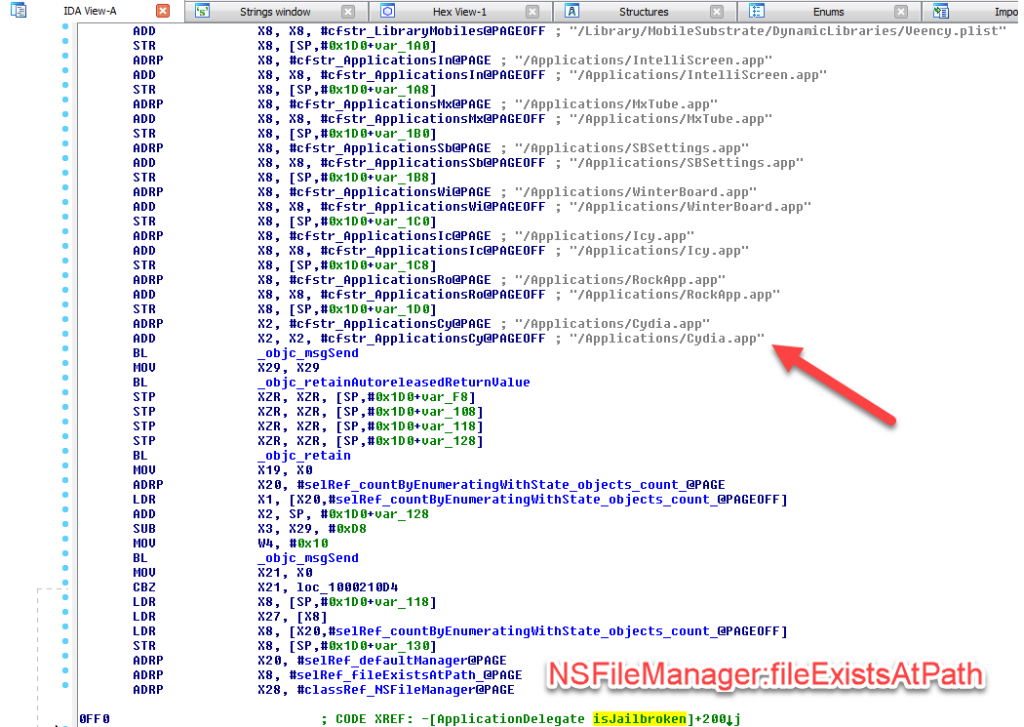
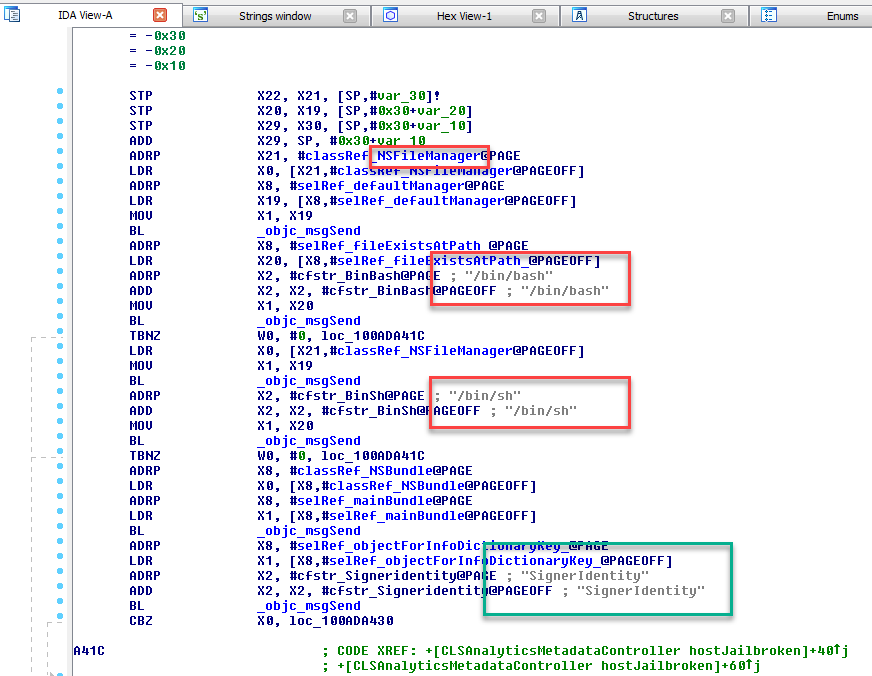
the first thing what i do is checking strings and function names for “jailbreak” or “cydia“. most likely Citrix is checking for files, that are only available on a jailbroken devices. here are some screenshots of related references that i have found:
pretty straight forward. Citrix uses the NSFileManager Class with the Method fileExistsAtPath to check for the presence of the referenced files. but actually quite some checks will even fail on a jailbroken phone, because these apps/tweaks dont exist anymore. a lof ot them were used in earlier jailbreaks, but nobody is using iOS 6 anymore – Citrix Receiver requires at least iOS 9 anyway and therefore most of these checks are obsolete.
another funny thing is the “SignerIdentity” reference. this is not jailbreak related, but checks if an app has been pirated (means, decrypted with Clutch for example) – but nobody is going to pirate a free app?!?!?
Bypassing the Jailbreak Detection
we have a couple of options here:
- we could binary-patch it (which would not work after an update of the app and we would need to patch the SignerIdentity aswell)
- Flex 3 is an app that can override functions without coding knowledge (but it costs 4$)
- Cyscript allows us to hook functions aswell
- using Frida we can use javascript to manipulate the code
- we can code a tweak (with theos) that spoofes the return values of these checks
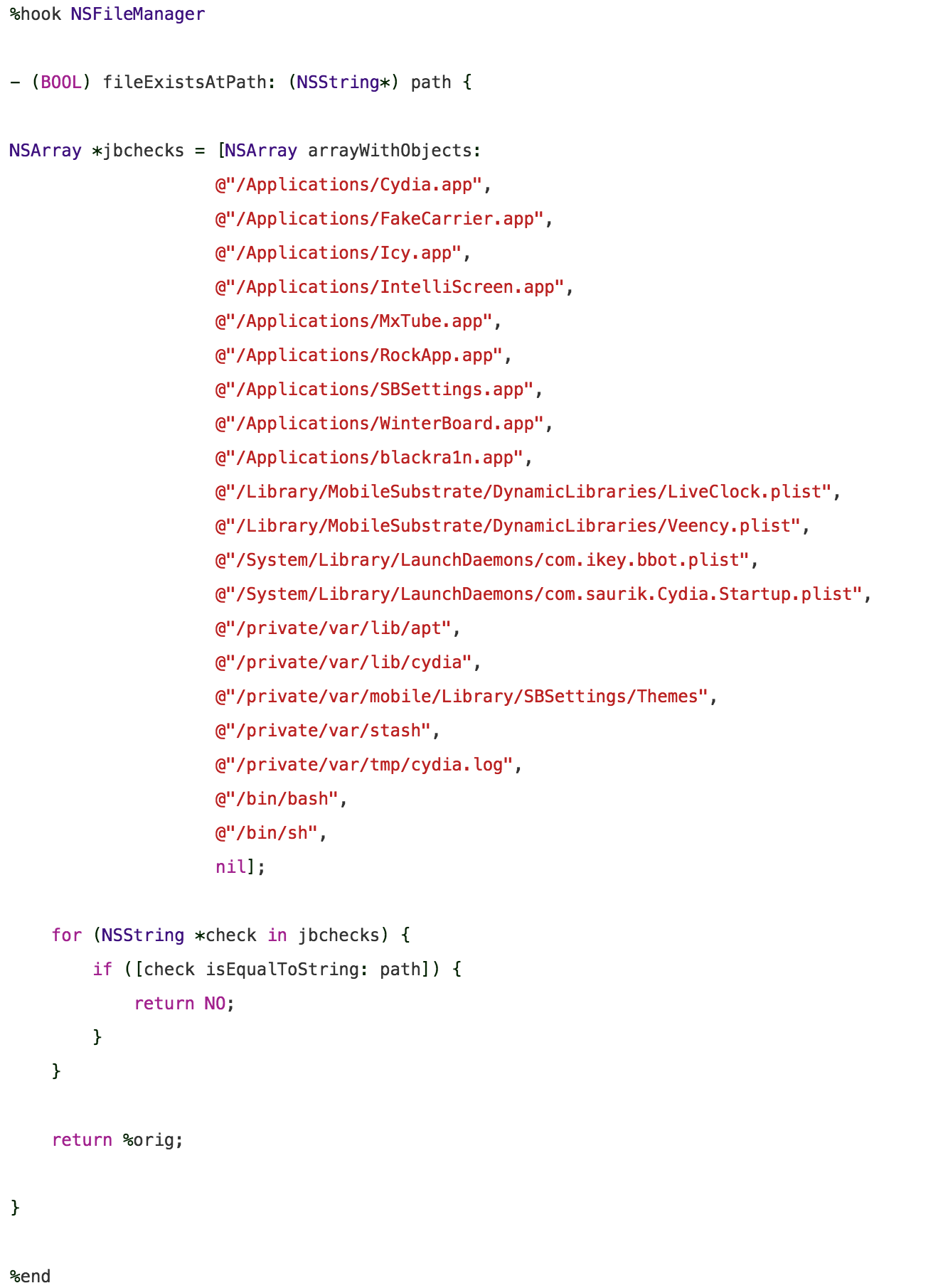
i decided to code a tweak myself. we could now hook into “isJailbroken” and return always “NO”. but there are multiple checks and therefore i decided to hook NSFileManager fileExistsAtPath, because this will work for all checks in the binary. i will only check if one of the paths matches and simply return “NO”.
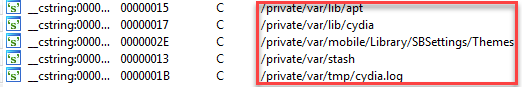
here is a list of all referenced files which are related to jailbreak:
/Applications/Cydia.app
/Applications/FakeCarrier.app
/Applications/Icy.app
/Applications/IntelliScreen.app
/Applications/MxTube.app
/Applications/RockApp.app
/Applications/SBSettings.app
/Applications/WinterBoard.app
/Applications/blackra1n.app
/Library/MobileSubstrate/DynamicLibraries/LiveClock.plist
/Library/MobileSubstrate/DynamicLibraries/Veency.plist
/System/Library/LaunchDaemons/com.ikey.bbot.plist
/System/Library/LaunchDaemons/com.saurik.Cydia.Startup.plist
/private/var/lib/apt
/private/var/lib/cydia
/private/var/mobile/Library/SBSettings/Themes
/private/var/stash
/private/var/tmp/cydia.log
/bin/bash
/bin/sh
even most being obsolete, i will include them in my tweak anyway. this can be done by using a simple string array and looping trough it on each fileExistsAtPath call. i will save you more headaches and give you the code straight away:
you can find the project on my github.
in theos we have just to make sure, that the tweak only applies to the Citrix Receiver App by specifying the bundle identifier com.citrix.ReceiveriPad.
make package in theos, will create a .deb file, which we can install with SSH or Fileza File Manager. and voila: we can connect with a jailbroken iPhone/iPad to our Citrix environment and the annoying message is gone too:
i have uploaded this tweak to thebigboss.org repository in cydia and you can install it directly from there – its free.
that was fun, wasnt it? i hope you enjoyed it aswell. cya in my next article 😉
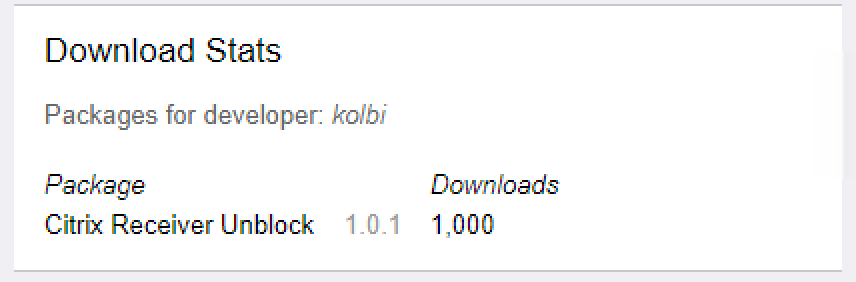
UPDATE 23.10.2017 20:25: wohooow. we have hit 1000 downloads already! i didnt expect so many people using Citrix Receiver on jailbroken devices.
if you want to donate, i would appreciate it very much. just use one of the following options:
BTC: 1G7HETp7j5dq422mTg1VNB1yph9m3eKgX1
LTC: LdmnKE7SnKAzKPrs6MrrPFXskuP1qRVBcD
ETH: 0x89c83770e89ae08e856EE239e477BC758FCf3Bf8
XMR: 47y7gzD2DmjSBhKyaxQ2C7RUpLgwzr2hYGu2Ui6NcAi2feChfVR99nhBvJPQxPqhEpRfuy9pAr5ypghETPWQ3MQGCdYSK3u
PayPal: https://www.paypal.me/Kolbicz
Thank you!

Leave a Reply
You must be logged in to post a comment.